A couple of months ago it was revealed that a hacker was selling a database with almost 500 million records extracted from LinkedIn and since then things do not seem to have improved for users of this networking platform, as it has just been revealed that a new threat actor is selling more than 700 million records of the platform.
The seller, identified as TomLiner in dark web forums, claims he has access to 700 million records and even posted a sample with 1 million records to prove the leak is legitimate.
Privacy Sharks researchers mention having accessed the leaked sample, confirming that the compromised records include full names, email addresses, phone numbers and other profile details.
In a statement related to the previous incident, LinkedIn mentioned that the leak reported in May contained a large amount of information from websites and companies with profiles on the platform, in addition to user data that by default is publicly visible. The company confirmed that this incident could not be considered a data breach, as it only included information that is available to any user.
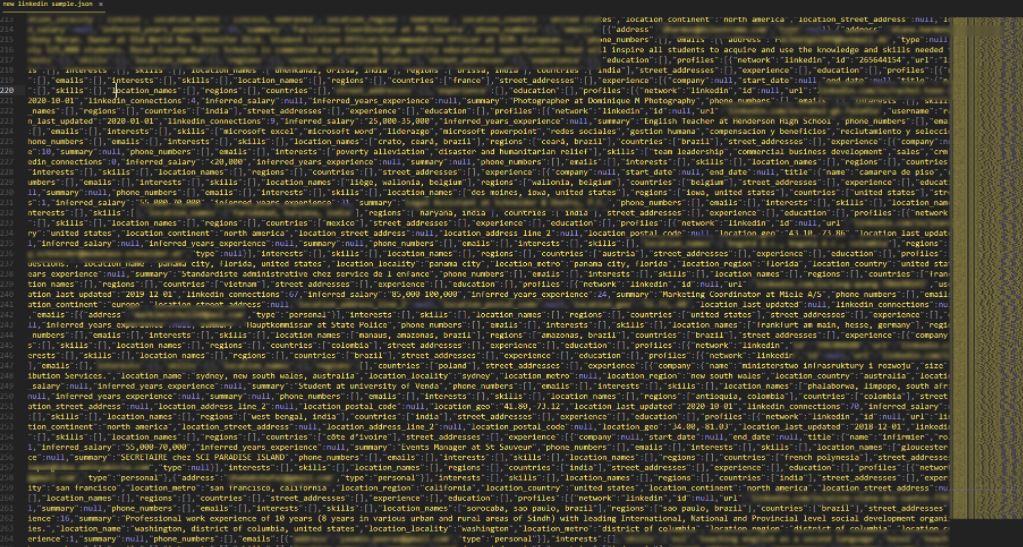
This time, the leaked database also appears to be composed of publicly available information, data extracted from other leaks, and duplicate records. However, the seller claims that the entire database includes all kinds of confidential records.
LinkedIn has already spoken out about it, sending a brief message to privacy shark experts: “We are still investigating this incident, although our first inquiries seem to confirm that the leak was extracted from both LinkedIn and other sources. Data mining from LinkedIn is a violation of our Terms of Service and we are constantly working to ensure that the privacy of our members is adequately protected.”
Although the password and email address leak in this incident has not been confirmed, experts recommend That LinkedIn users update their passwords for this and any other online platform, in addition to enabling multi-factor authentication to prevent some hacking variants such as brute force or credential stuffing attacks.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
