The KDE Discover team of researchers has published countless reports on how popular desktop applications handle user-provided URIs, which in certain cases allows the exploitation of some security flaws in Linux PlingStore websites. During the investigation, a cross-site scripting (XSS) flaw was detected on Pling-based e-commerce websites, and a remote code execution (RCE) flaw on PlingStore. These flaws were only corrected in June 2021.
As some users may already know, Pling is a content management and installation application for OCS-compliant websites such as pling.com, gnome-look.org, and appimagehub.com, among others. It allows you to download, install and apply desktop themes, icon themes, wallpapers or mouse cursors directly in various desktop environments using the “Install” button.
XSS vulnerability
Experts retrieved and displayed data from https://store.kde.org. While creating their own list to analyze discover’s URI handling, an XSS flaw was detected.
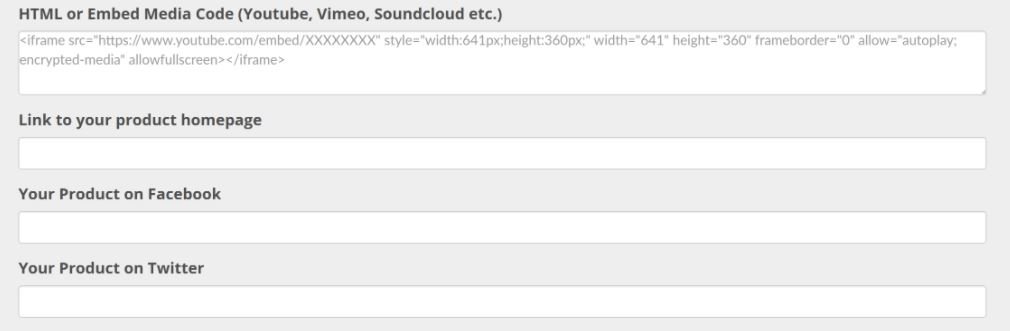
While a first simple XSS payload didn’t work, it was enough to first add an iframe and then the malicious JavaScript payload on a separate line to exploit this flaw:
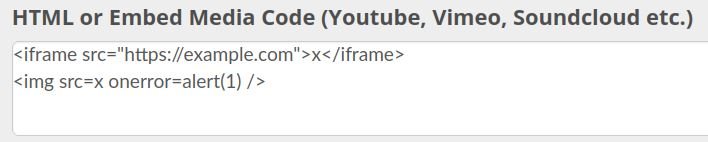
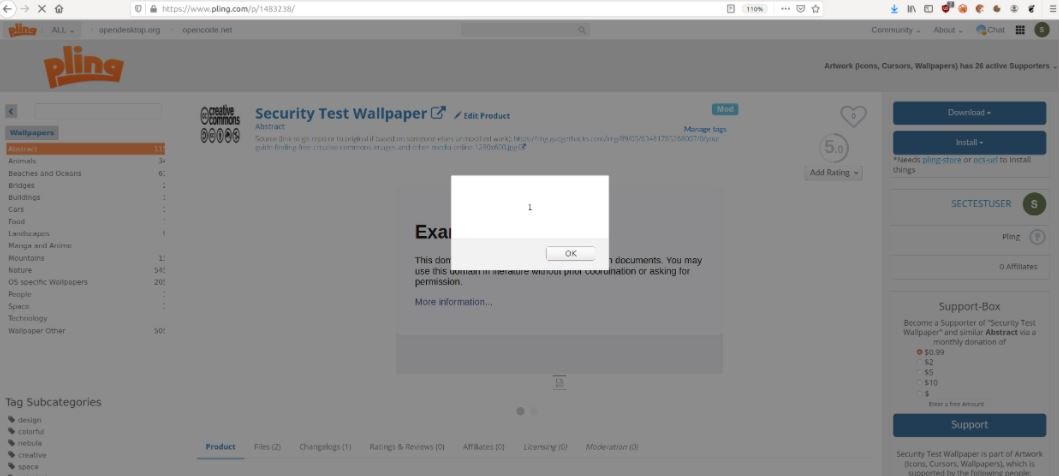
This XSS error could be used to modify active listings or publish new listings to the Pling store in the context of other users, resulting in an XSS condition.
Remote code execution
All Pling-based stores advertise the use of the native PlingStore app, an Electron app that can display the different websites and allows easy installation of the app with 1 click.
When the PlingStore application starts, it also starts ocs-manager, a local WebSocket server that listens for electron.ocs-manager messages implements several functions that will be invoked by the Electron application to retrieve information or trigger actions. Experts found that by combining three calls to these functions, it is possible to execute arbitrary code.
During the tests, the experts managed to trigger three actions:
- Call ItemHandler::getItem to download an AppImage from any URL as type bin
- Call ConfigHandler::getAppConfigInstallTypes to filter the full path of the bin directory
- Call SystemHandler::openUrl with the AppImage path as an argument
If the XSS error is triggered within the Electron application, the payload can establish a connection to the local WebSocket server and send messages to execute arbitrary native code.
Web browser abuse
Because web browsers do not implement the same-origin policy for WebSocket connections, it is important to validate the origin server or implement an additional authentication mechanism using WebSocket.
Such a situation does not apply in ocs-manager, so any website in any browser can initiate a connection to the WebSocket server, and ocs-manager will accept any command sent without further checks.
The attack is completed by directing users to a malicious website, which is possible to do from any browser with PlingStore running in the background. In their proof of concept (PoC), the experts used a payload through an AppImage file to launch an xmessage with a custom string as an argument to complete the code execution.
Experts demonstrated the exploitation of multiple vulnerabilities that pose severe security risks to e-commerce website operators. As a recommendation, developers of affected products should perform strict scans to address all possible flaws detected.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
