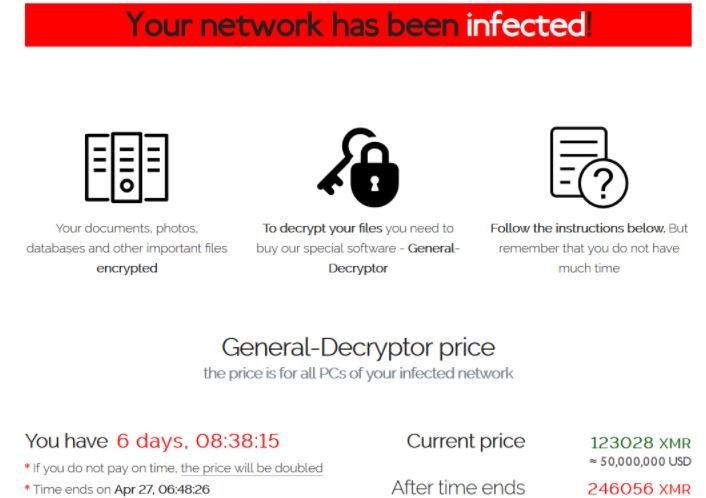
Any tech company can be the victim of an attempted extortion. According to a security report, REvil ransomware operators threatened Apple to reveal plans for many products that would be revealed at the Apple Spring Loaded event if they did not meet their economic demands. Hackers want Apple to pay the ransom by May 1 to prevent the information from being revealed.
Ransomware operators tried to extort Apple just days after Quanta Computer, one of Apple’s most important trading partners, refused to start negotiations with hackers to agree to pay a ransom after a purported massive breach of sensitive data.
As you’ll recall, Quanta is a Taiwan-based company dedicated to hardware manufacturing for devices such as Apple Watch, Macbook Air and Macbook Pro. Quanta also work with other technology companies such as Dell, HP, Alienware, Lenovo, Microsoft and Cisco.
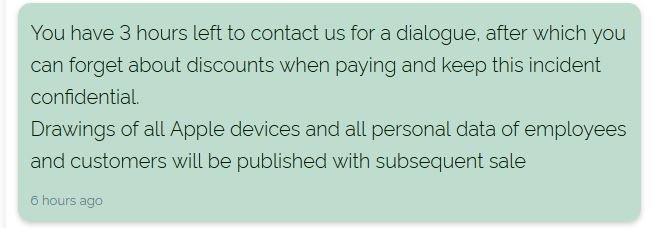
REvil has leaked more than a dozen diagrams related to MacBook components on its dark web platform used to publish victim leaks. Hackers also warned that all leaked schemes will be published in the coming days unless the company decides to pay the required ransom. Apple and Quanta spokespersons were not available to comment during the hours following this leak.
About attack operators, cybersecurity experts point out that REvil is a ransomware-as-a-service (RaaS) platform characterized by its affinity to recruiting advanced hackers capable of compromising corporate and government networks. When the operators of an attack get a ransom, the profits are split between the creators of the ransomware and the hackers responsible for the attack.
Experts attribute to REvil a key role in the latest wave of cyberattacks detected in companies such as Acer, Pierre Fabre and Asteelflash, which would have generated up to $100 million in losses. Specialists also believe that hackers are modifying their mode of operation to gain a dominant position while negotiating a ransom, which they believe could ensure them much higher profits.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
