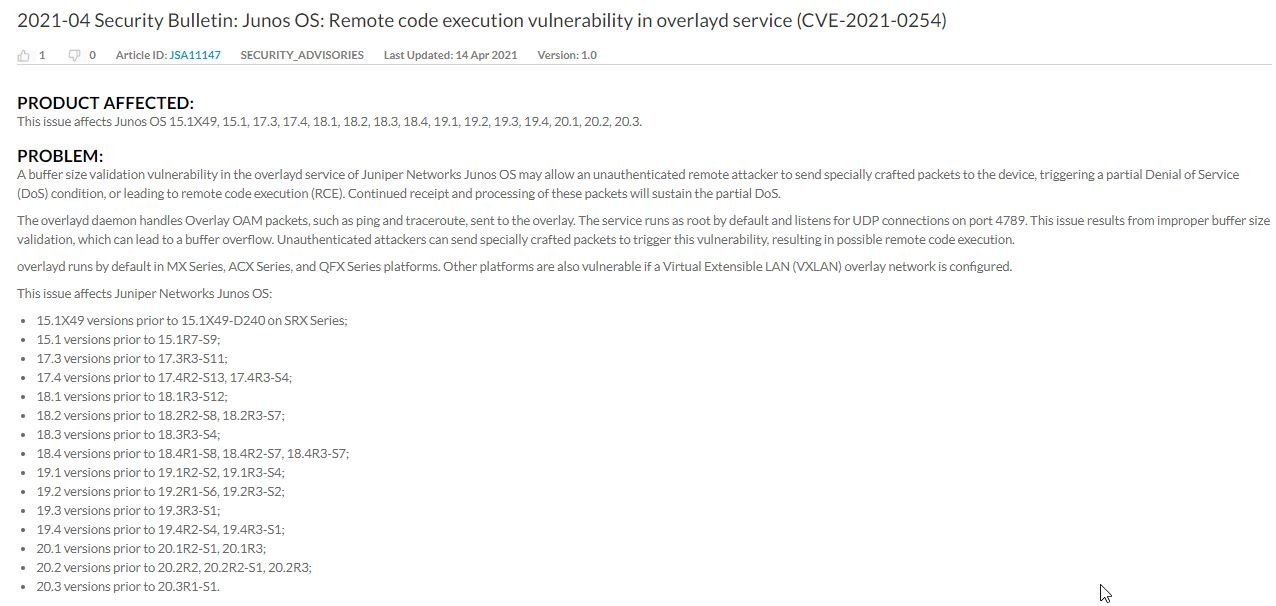
Network and cybersecurity solutions company Juniper Networks announced the patching of a vulnerability that would allow threat actors to hijack sessions on affected devices. Tracked as CVE-2021-0254, the flaw directly impacts the operation of Junos, Juniper Networks’ operating system.
The flaw was discovered by researcher Nguyễn Hoàng Thạch, also known as D4rkn3ss, who mentions that this is the most serious vulnerability ever identified in a Juniper product, which was reported more than six months ago.
Juniper’s security alert also mentions that the vulnerability could be exploited by unauthenticated remote threat actors to perform arbitrary code execution attacks or trigger denial of service (DoS) conditions. Abuse of this flaw requires sending specially designed packages to the target system, so generating the DoS condition would be relatively easy.
On the other hand, D4rkn3ss mentions that an attacker who successfully exploits this vulnerability could gain root access to the target system and then install a backdoor or make any modifications to the target device settings. In addition, exploitation does not require the interaction of the target user and can be chained with other attacks.
The report notes that remote attacks are theoretically possible, although devices vulnerable to this attack are generally not exposed on the Internet, so an opposite would result from multiple unusual configuration errors.
Juniper also mentions that the daemon handles Overlay and OAM packets, a service run as root by default and listening for UDP connections on port 4789: “This issue exists due to incorrect validation of buffer size, which could lead to overflow and eventual remote code execution,” the company notes.
This daemon runs by default on MX and ACX routers, and is also present on Juniper QFX switches. The company concludes by mentioning that no evidence of active exploitation of flaws has been found, although they point out that the attack can be launched against other default configurations, so they recommend that administrators audit the security of their network devices.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
