Many users believe that Linux-based systems are invulnerable, although this is not entirely true. Like other solutions, these systems are vulnerable to threats such as rootkits, ransomware, viruses and many other security risks.
Public and private organizations around the world have worked to adopt security best practices, developing tools for malware detection and security flaws, as well as complex monitoring tasks. This type of software is usually very expensive, although fortunately there are always more accessible alternatives. Below, pentesting specialists from the International Institute of Cyber Security (IICS) present the 7 best free tools for Linux server protection.
LYNIS
Lynis is probably the most popular security tool among Linux professionals, and also works on UNIX and macOS-based systems. According to pentesting experts this is open source software that has been distributed under the GPL since 2007.
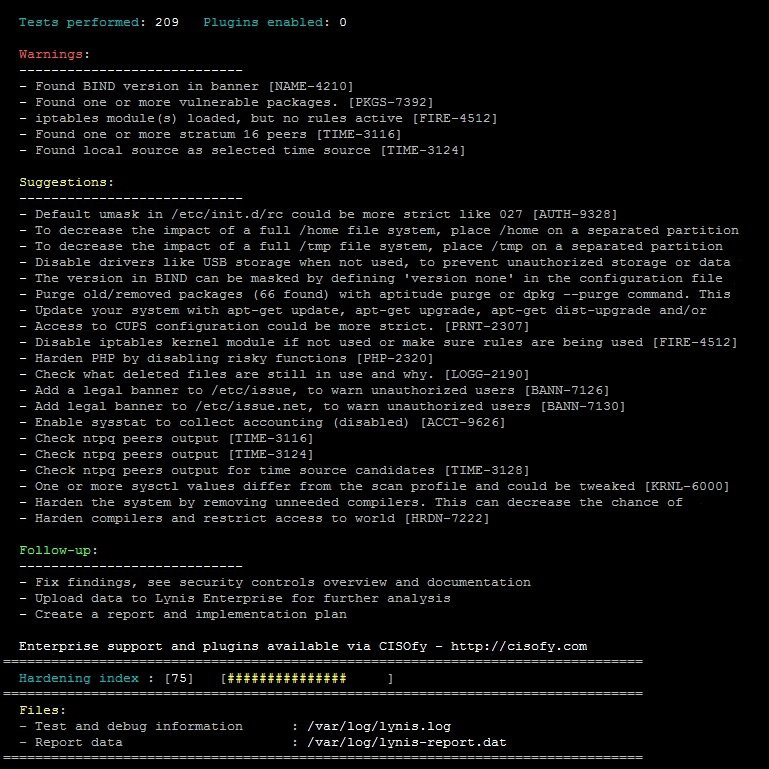
Developed by Michael Boelen, this tool does not require installation and can be downloaded from your Git repository. Users can download either version, either for individual use or for organizations.
CHKROOTKIT
This is a utility for scanning systems for rootkits, a term referring to a type of malware triggered by threat actors for malicious purposes. If these packages have Linux-based servers, rootkits can be a real problem.
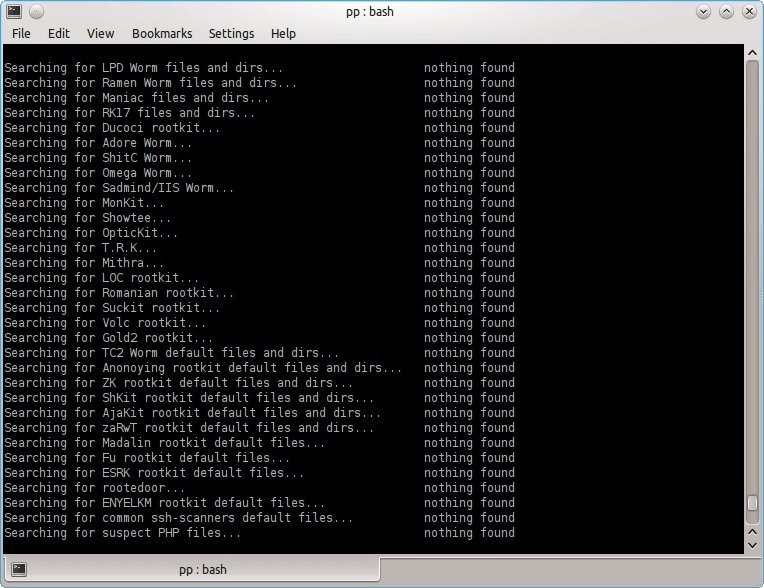
Chkrootkit can be started from both an alternate directory and an external drive. The various components of the tool look for deleted entries in the wtmp and lastlog files, finding trace entries or rootkit configuration files and checking the hidden entries in the /proc or readdir calls.
RKHUNTER
Michael Bolin developed Rkhunter in 2003 to assist in the detection of rootkits and other vulnerabilities in Linux systems. Rkhunter carefully scans files, whether hidden or visible, default directories, kernel modules, and misconfigured permissions for security flaws, pentesting experts mentioned.
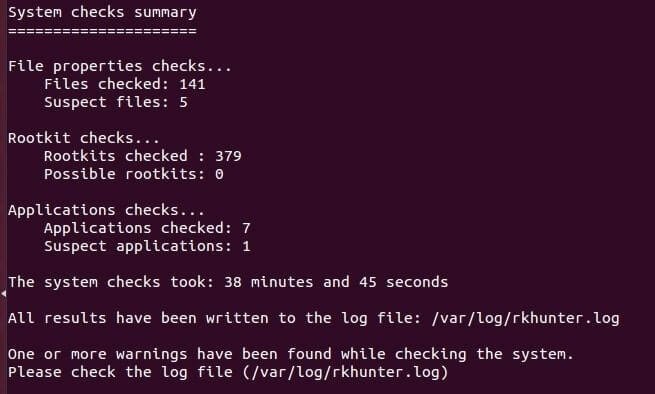
After a routine check, the tool compares the results with correct and secure database records and searches for suspicious software.
CLAMAV
This is an open source antivirus written in C++ that helps detect viruses, Trojans and other threats. Many users use it to scan personal data, including emails, for malicious files of any kind, in addition to scanning servers.
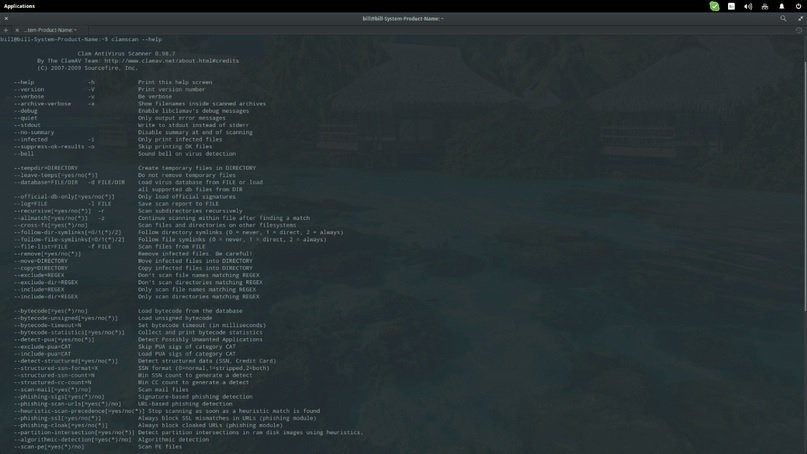
At first this tool was available only for UNIX, with third-party versions for Linux, BSD, AIX, macOS and OpenVMS. ClamAV automatically updates your databases to identify the most recently discovered threats, as well as scan commands and perform your processes very efficiently.
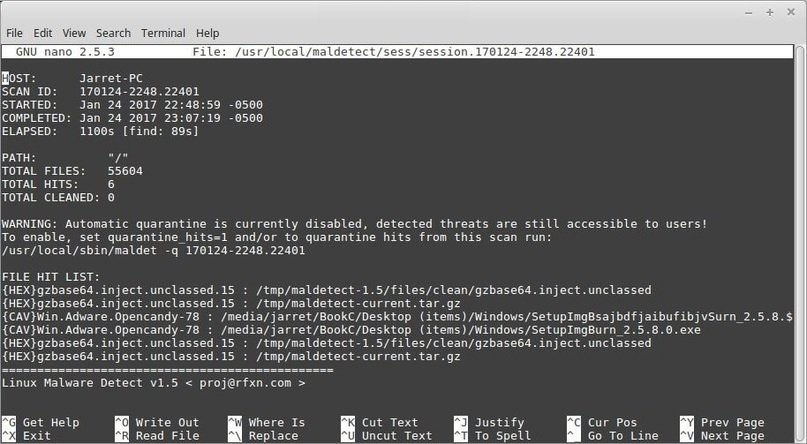
LINUX MALWARE DETECT (LMD)
This is a very popular tool to detect common security threats on Linux systems. Like other malware analysis solutions, LMD uses a constantly updated database to prevent recent security threats, pentesting experts say.
RADARE2
This is a binary analysis and reverse engineering framework with high security threat detection capabilities. According to pentesting experts, this tool can identify infected files, provide the user with tools to manage them and neutralize potential threats.
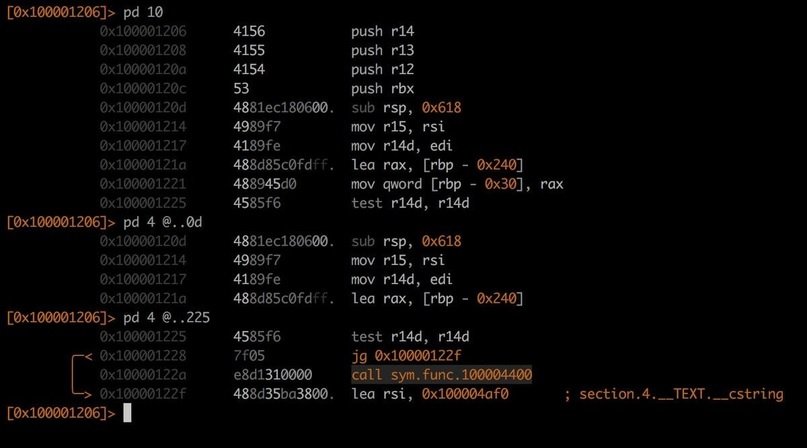
One of its hallmarks of Radare2 is that users should not use the command line to perform static and dynamic analysis tasks, making it ideal for any type of binary data exploitation.
OPENVAS
This is a vulnerability management and analysis system designed for organizations of all sizes, helping to identify invisible security issues in the infrastructure. This product was originally known as GNessUs until the new owner, Greenbone Networks, changed its name to OpenVAS.
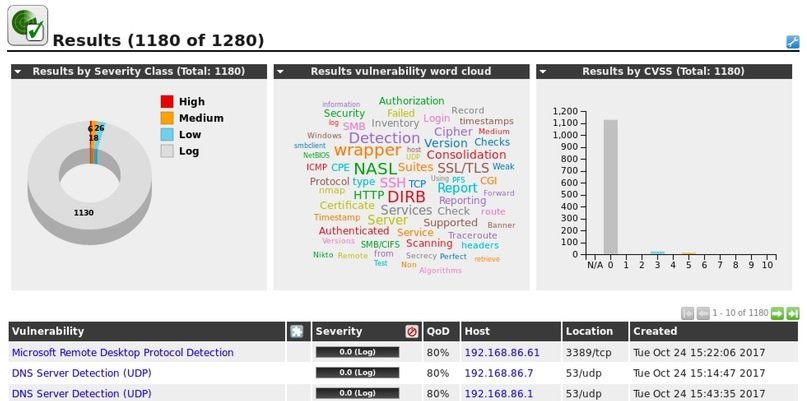
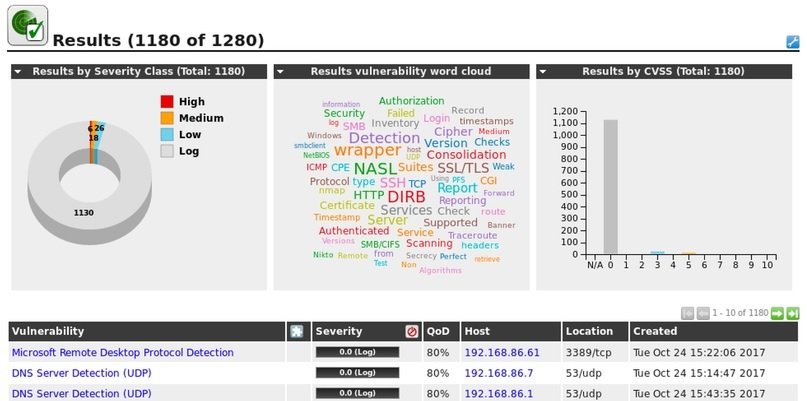
Pentesting experts use OpenVAS because of its fast scanning capability, and it represents an excellent opportunity to eliminate configuration errors. The OpenVAS source code is available under the GNU GPL license.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
