As part of its update package for April 2021, SAP released 14 recommendations and 5 security patches to address various issues in its products, including a bug tracked as CVE-2021-27602 which was described as a remote code execution error that received a score of 9.9/10 according to the Common Vulnerability Scoring System (CVSS).
These flaws appear to allow authorized users in SAP Commerce Backoffice software to inject malicious code into system rules by abusing the scripting capabilities of the rule engine: “Successful exploitation of these failures could trigger remote code execution on the affected system, being able to critically impact compromised operations,” notes the report prepared by security firm Onapsis.
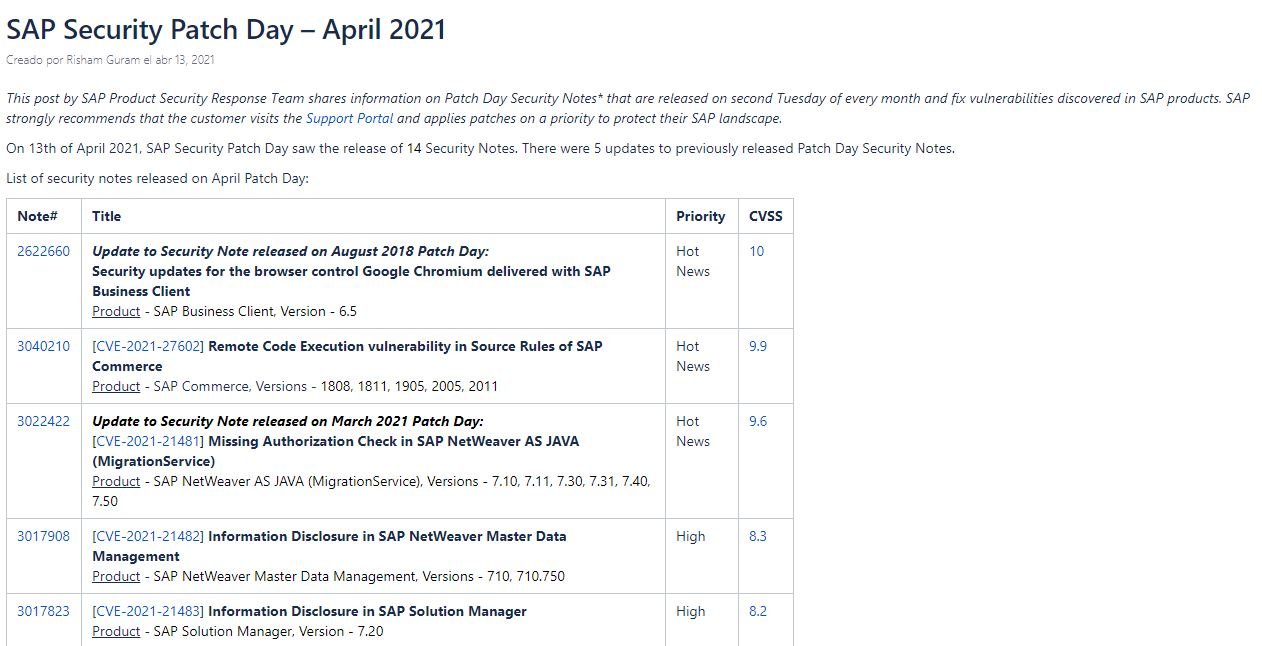
The company issued some additional security validations to mitigate the risk of exploitation, in addition to issuing two additional recommendations to prevent other risks: “The first of these recommendations includes an update to SAP Business Client’s Chromium-based browser, while the second recommendation relates to missing verification in NetWeaver AS JAVA,” the report notes.
April updates also include patches for the following failures:
- CVE-2021-21482: Potentially confidential information disclosure vulnerability in NetWeaver Master Data Management
- CVE-2021-21483: Potentially confidential information disclosure vulnerability in SAP Solution Manager
- CVE-2021-21485: Potentially confidential information disclosure vulnerability in NetWeaver AS for JAVA
- CVE-2021-27608: Quoteless service path error in SAPSetup
The remaining reports refer to security flaws with an average severity rating in products such as NetWeaver AS for Java, NetWeaver AS for ABAP, Integration Builder Framework, ESR Java Mappings), Focused RUN, and HCM Travel Management Fiori Apps V2.
Affected deployment administrators are advised to apply available patches as soon as possible to keep their networks safe from hackers. A study that SAP and Onapsis published last week revealed that in some cases, threat actors begin targeting newly patched vulnerabilities a few days after security updates are released, so administrators should not miss a single day to patch their systems.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
