Cybersecurity specialists report detecting a couple of sophisticated phishing campaigns targeting around 10,000 users from different versions of Microsoft operating systems. In both campaigns, which copy corporate images from DHL and FedEx, threat actors seek to steal the credentials of affected users for further attacks.
These campaigns were detected by experts at security firm Armrblox, who mention that the title lines of these phishing emails should be attractive to attacked users in order to increase the chances of success of the attack: “The message includes legitimate documentation from these companies, making detection difficult.”
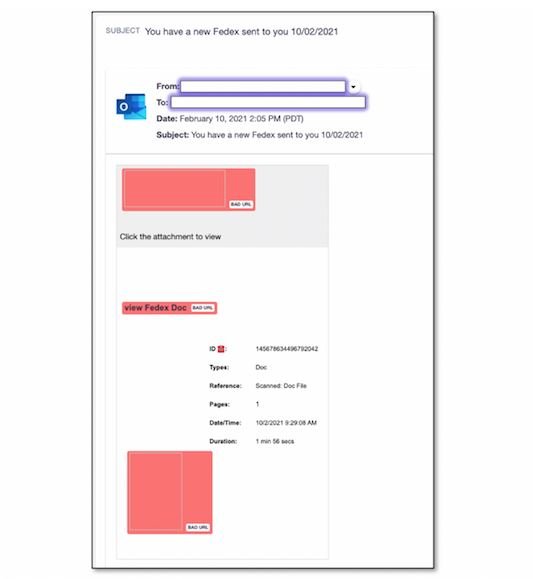
The message assures the user that someone sent him a package through the aforementioned companies, plus some additional data to give greater credibility to the scam. This message includes an attachment and a link that redirects users to the external malicious website. If users click on the link, they will be redirected to a site hosted on Quip.
The researchers claim that threat actors have increased their interest in using legitimate platforms such as Quip and Google Sites: “Criminals use free versions of these services, generating trust among potential victims and making them more likely to fall into deception.”
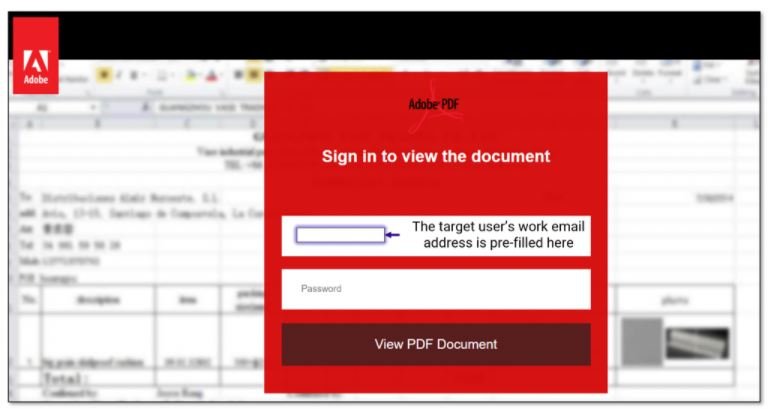
The Quip site contains the logo of one of these companies, as well as including the phrase: “You have received some incoming files”. This site performs another redirect to a website similar to the Microsoft login page hosted on Google Firebase, a developer platform.
If the target user enters their credentials on this phishing platform, the same website is reloaded in conjunction with an error message: “This could point to some backend validation mechanism that verifies that users enter legitimate information,” experts note. Hackers could also be using this campaign to collect thousands of email addresses and passwords.
In addition to using the shipping company theme, threat actors have found COVID-19 a topic of great interest worldwide, making it easier to deploy phishing campaigns announcing alleged vaccines, medical treatments and even follow-up applications to coronavirus patients. To learn more about information security risks, malware, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) website.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
