In mid-January the main operator of the illegal platform Joker’s Stash announced the definitive shutdown of its trades, making it very clear that it had no intention of returning afterwards. This does not mean that cybercrime has run out of resources, as other similar platforms are looking to stay with customers from which it became the most important illegal web to buy stolen credit cards.
According to a report prepared by security firm Flashpoint, among the illegal platforms competing to win over former Jokers’ Stash customers are Brian’s Club, Ferum, Trump’s Dumps, Vclub, UniCC and Yale Lodge.
Specialists mention that, so far, Brian’s Club seems to have taken the lead in this competition. One of the main indicators for reaching this conclusion is that this platform recently replaced Joker’s Stash as the official sponsor of Omerta, one of the most important underground forums, as well as starting an advertising campaign on other similar platforms even before the closure of Joker’s Stash.
With nearly a decade on the black market for payment cards, experts estimate Brian’s Club has around 5 million cards stolen for sale, although it still has a long way to go to even approach the 30 million units stored in Joker’s Stash systems.
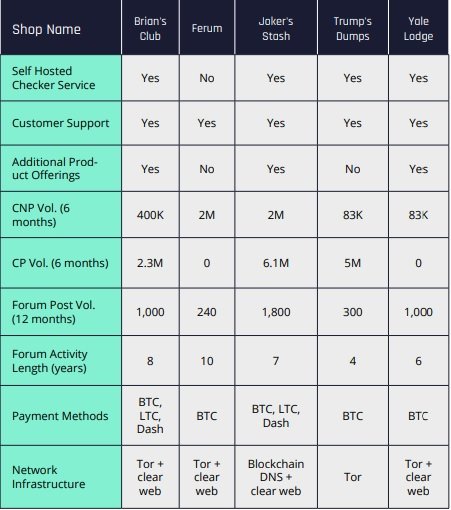
On the other hand, experts mention that Yale Lodge also appears to have taken a relevant position on the black market, mainly because it operates a store of stolen payment cards on the Tor network in addition to a verification service for customers to verify that they are purchasing existing payment cards. Researchers believe that Yale Lodge’s main disadvantage over other platforms is the collection of a registration fee, plus the platform requires users to make a minimum deposit of $200 USD.
On top emerging platforms, experts point to Trump’s Dumps as one of the most ambitious projects, as it also features a payment card verification tool. Vclub also burst strongly, although when analyzing some forums on dark web experts detected multiple complaints about this service.
Many of the cybercriminal groups work closely with such platforms, so cybersecurity organizations and law enforcement agencies need to be aware of the latest trends to design better security strategies. To learn more about computer security risks, malware, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) website
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
