Cybersecurity specialists mention that a malicious hacking group discovered that it is possible to abuse Google Chrome sync feature in order to send infected commands to firewalls and other network security mechanisms. As users will remember, this feature allows you to store copies of Chrome bookmarks, browsing history, passwords, and browser settings on Google’s cloud servers.
Specialist Bojan Zdrnja mentions that, during a recent incident response process, he discovered that a malicious extension was abusing Chrome’s sync feature to communicate with a C&C server, extracting data from victims through infected browsers.
The expert mentions that in their investigation threat actors gained access to sensitive data on the compromised system, downloading a Chrome extension that was uploaded via developer mode in the browser. This extension, disguised as a security plugin developed by the security firm Forcepoint, included malicious code to abuse the sync feature in order to allow threat actors to take control of the compromised browser.
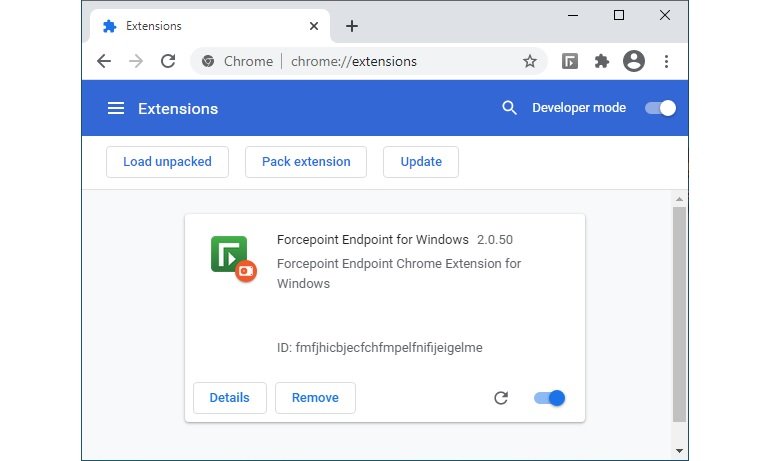
“Threat actors seek to use this extension to manipulate data in an internal web application that victims have access to,” Zdrnja says.
The malicious code found in the extension suggests that threat actors used the malicious add-on to create a text-based field to store token keys, which would then sync with Google’s cloud servers as part of the sync feature: “To set up, read, or delete these keys, cybercriminals only need to log in with the same Google account in another Chrome browser to communicate on the victim’s network by compromising Google’s infrastructure,” the researcher says.
In this way criminals use the malicious extension as an extraction channel from inside corporate networks to an attacker’s Chrome browser instance or as a way to control the infected browser from afar, avoiding local security defenses.
Because stolen content or subsequent commands are sent through Chrome’s infrastructure, none of these operations would be detected as malicious activity on most corporate networks, where Chrome generally operates unrestricted. The researcher completed his report by asking companies exposed to use Chrome’s business features and group policy support to block and control potentially malicious extensions.
For further reports on vulnerabilities, exploits, malware variants, cybersecurity risks and information security courses fell free to visit the International Institute of Cyber Security (IICS) websites, as well as the official platforms of technology companies.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
