Security issues related to the use of messaging apps are not just about privacy issues, but these apps should also receive constant updates to prevent leaks or cyberattacks. This is a topic of great interest to Google Project Zero experts, who have discovered multiple security flaws in messaging apps such as Signal, Facebok Messenger, Google Duo, JioChat, among others.
Usage of WebRTC and SDP
Most popular messaging applications use WebRTC for their video calling functions, although connections are created by exchanging call settings using peer-to-peer Session Description Protocol (SDP), a process known as signaling. This process works by sending an SDP offer from the end of the caller, which callee must respond to with an SDP response.
As part of this offer/response exchange, the ability of the two pairs to exchange SDP candidates with each other and negotiate a real connection between them is also optionally included. Further, a WebRTC framework known as Interactive Connectivity Establishment (ICE) details the methods used for this communication, regardless of network typology.
When peers agree on a compatible candidate, each of them uses that candidate’s SDP to build and open a connection in which the information will begin to circulate during the video call. In this way, both devices share with each other the information needed to exchange audio or video over the peer-to-peer connection. Before this relay happens, the captured media data must be attached to the connection using a function called tracks.
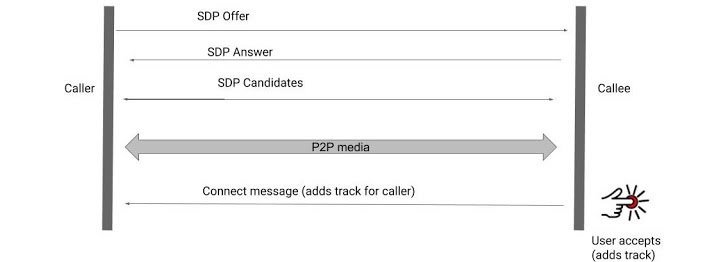
Although at this point in the process it is expected to obtain the user’s consent before starting audio and video streaming, Project Zero experts mention that abnormal behaviors sometimes occur depending on each application.
According to Project Zero researcher Natalie Silvanovich, these flaws allow the camera of the receiving device to be activated without prior authorization due to some logical errors in the signaling process.

Facebook Messenger
Exploiting this flaw could have granted threat actors to launch the application to initiate calls and send specially designed messages to affected users with a session logged in to the web version of the platform, resulting in receiving audio and video from the target device.
Google Duo
A race condition between disabling the video and configuring the connection could have resulted in the calling device filtering video packets into unanswered video calls.
JioChat and Mocha
Adding candidates to offers created by Reliance JioChat and Mocha Android apps allowed a caller to force the target device to send audio and video without the user’s consent. These faults were corrected last year.
Signal
The flaw detected in Signal would allow users who make voice calls through this app to listen to the environment of the user receiving the call, since the app does not verify whether the device receiving the call is the same as receiving the connection message. The flaw was fixed in September 2019.
The specialist believes that these security flaws do not exist due to bad practices by developers, but exist because of the implementation of the serialization process: “It is noteworthy that all failures were detected in peer-to-peer calls, indicating that more work is needed in this area in the future,” Silvanovich concludes.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
