A hacker group is illegally accessing multiple verified Twitter accounts with the aim of deploying cryptocurrency fraud allegedly gifted by millionaire Elon Musk. This strategy has been previously deployed, even estimated that in 2018 traders made about $180,000 in fraudulent profits.
A few days ago, security researcher MalwareHunter discovered an increase in the number of verified accounts that have been compromised as part of this attack. As we can see below, Elon Musk’s verified account shows the so-called cryptocurrency gift campaign.
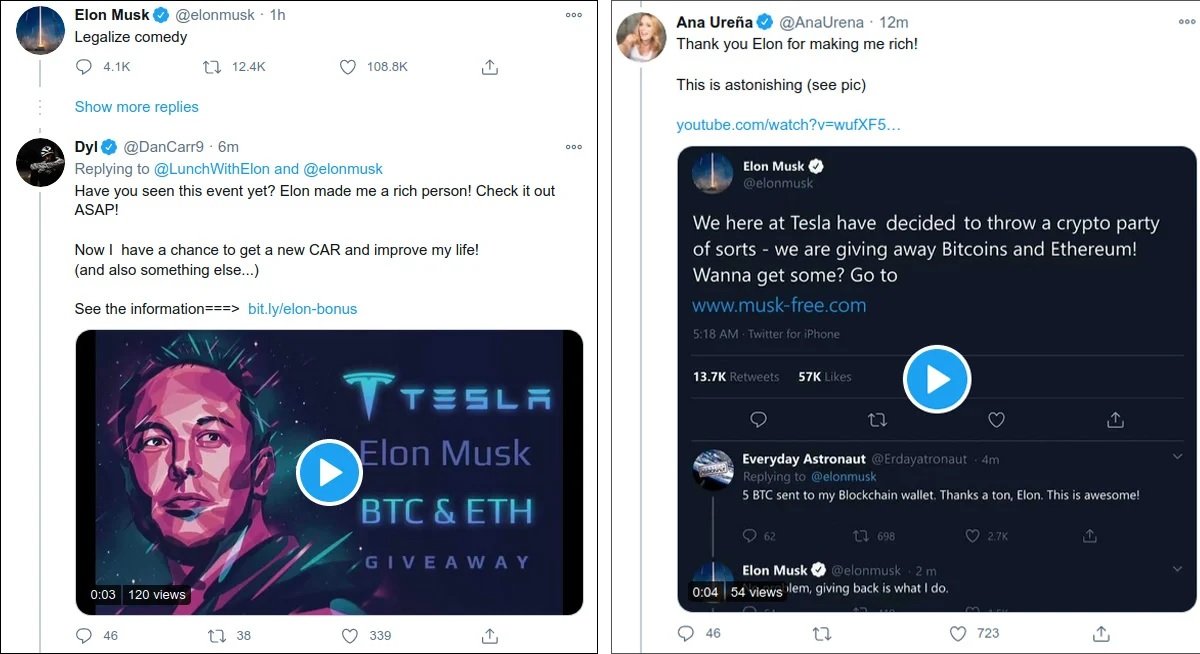
Tweets posted by scammers contain links that redirect users to Medium posts that contain more information about the fake draw, mentioning to victims that if they send cryptocurrency to the above address, they can receive twice their contribution.
Although the main theme of the scam remains the image of Elon Musk, some compromised accounts also offer alleged gifts from Tyler Winklevoss of Gemini Exchange.
Apparently the scam operators target accounts that have been inactive for a long time but have the verification seal provided by the platform, so they expect legitimate owners not to detect malicious activity. In addition, Twitter interrupted any account verification process after the attack last July, so a compromised account can be very attractive to threat actors.
Despite being a very passive attack variant, traders have already received more than $500,000 through the different Bitcoin addresses under their control. The Ethereum addresses used in this campaign have received just over $2,000.
Cybersecurity experts have sought to identify all cryptocurrency addresses potentially associated with this campaign, although cybercriminals are not ruled out to control more addresses that have not yet been detected. Users should remember that neither Elon Musk, Winklevoss twins nor any other eccentric millionaire is gifting cryptocurrency, even if this offer appears in a verified account.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
