The Federal Bureau of Investigation (FBI) has reported the detection of at least 100 fraudulent websites allegedly associated with federal agencies in the United States. These fake email accounts and domains are used by threat actors to mislead users for malicious purposes such as information gathering, spreading false reports, malware deployment, and bank fraud or identity theft, among other attacks.
This has become a common practice. Threat actors create fake domains with names almost identical to the real ones, changing only a few characters. Below is a list of all the malicious domains identified by the federal agency:
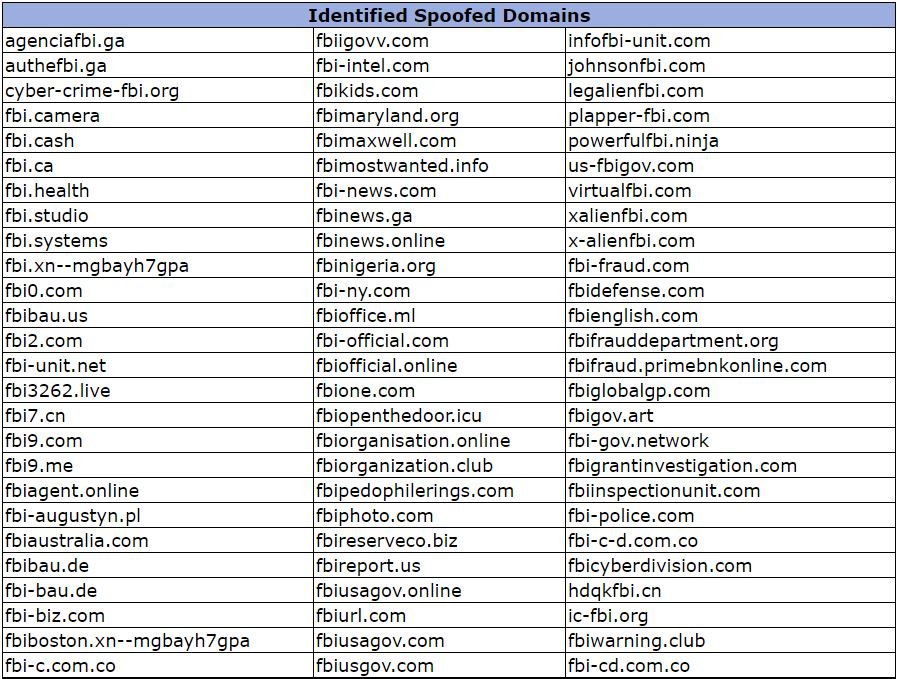
It is important that users remember that the official domain of the FBI is www.fbi.gov, so they should ignore any other similar domain. Sometimes threat actors use .com versions of the official website, making it difficult to identify between the official platform and fraudulent sites, however users should take time to verify the authenticity of the website.
In addition to verifying that the domain is authentic, FBI specialists have issued a series of recommendations:
- Check the spelling of web addresses, web sites, and e-mail addresses that appear reliable but may be imitations of legitimate election web sites
- Make sure operating systems and applications are updated to the latest versions
- Update your antivirus solutions and perform network scans regularly
- Do not enable macros in documents downloaded from email unless absolutely necessary
- Do not open unsolicited emails or attachments and never reply to unknown users
- Never provide personal information of any kind via email. No public organization requests personal data in this way
- If possible, use multi-factor authentication
Finally, if you find a suspicious web domain, do not hesitate to contact the appropriate authorities.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
