Cybersecurity specialists report finding a vulnerability in GNOME Display Manager (gdm) that could allow users with reduced privileges to create elevated accounts on Ubuntu systems. Although certain requirements for the attack must be met, experts point out that exploiting the flaw is relatively easy, as only a few simple commands are required in the terminal.
This attack abuses blocking on the AccountsService component, which tracks users registered to the system; gdm3 also displays the user login interface on Unix-like operating systems. Kevin Backhouse, a security specialist at GitHub, found a simple method to abuse Ubuntu systems in order to run an account setup routine for a new system.
Backhouse discovered that “gdm3” triggered the sequence required for the attack when ‘accounts-daemon’ in the AccountsService component does not run. Due to two flaws discovered by the researcher, system components can be blocked to remove privileges from the user’s account; this would allow threat actors to block the daemon with a segmentation flaw signal.
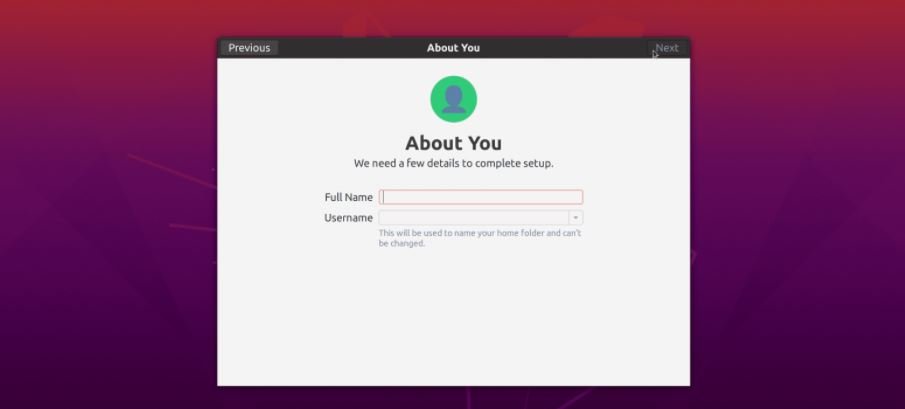
The delay is required to give time to log out of the current session or the user will be blocked. The two flaws, identified as CVE-2020-16127 and CVE-2020-16126 affect Ubuntu 20.10, Ubuntu 20.04, Ubuntu 18.04 and Ubuntu 16.04. Activation was possible by making a modification to the System Settings that did not require elevated privileges.
Through a video, Backhouse demonstrates how easy it was to exploit the gdm3 vulnerability in Ubuntu 20.04:
The report was released on Monday, specifying that Ubuntu and GNOME developers were notified in mid-October. Corrections are now available on official platforms. Users of compromised installations are asked to update as soon as possible.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
