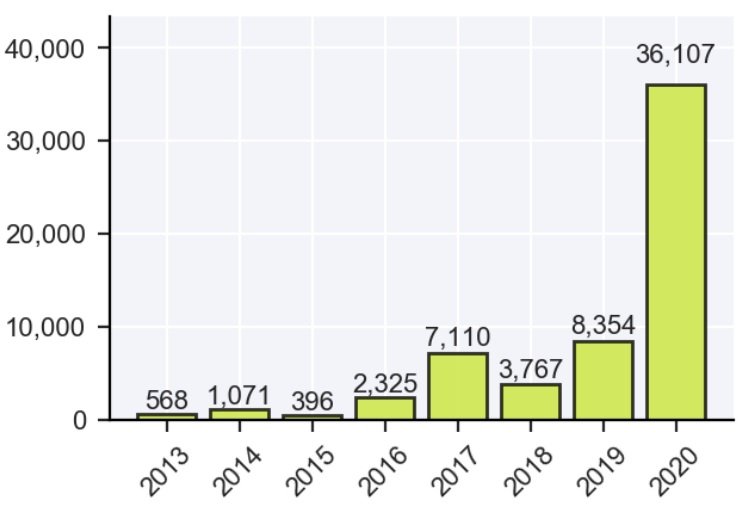
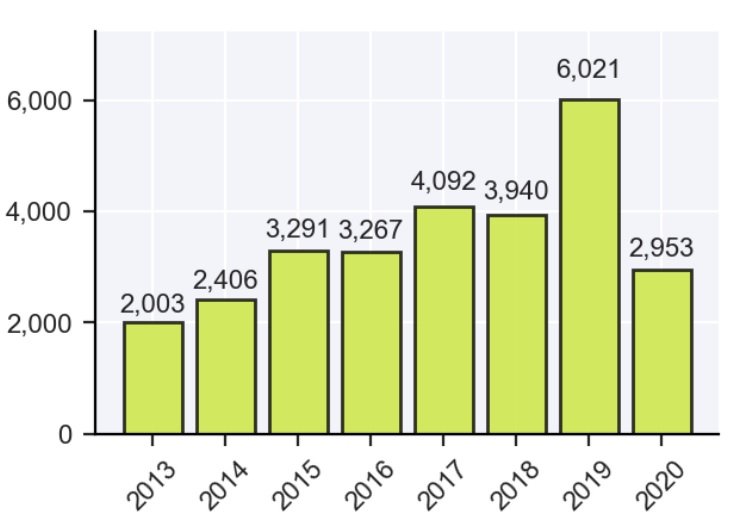
Records exposed by threat actors in data breach incidents during 2020 have already exceeded the figure recorded in 2019, a Report by Risk Based Security. According to the report, the figure reported up to the last quarter of 2020 is 36 billion records displayed, twice as high as the previous year.
In the first half of 2020 alone, 2,953 incidents were reported, compared to the less than 500 data breaches reported in the same period of the previous year, a trend that replicates in the analysis of these two years.
On the causes of these incidents, the first place is for threat actors, who caused 77.5% of the data breaches reported so far. Moreover, about 17% of these incidents were caused by data management errors, while the remaining 5.5% are due to undetermined causes.
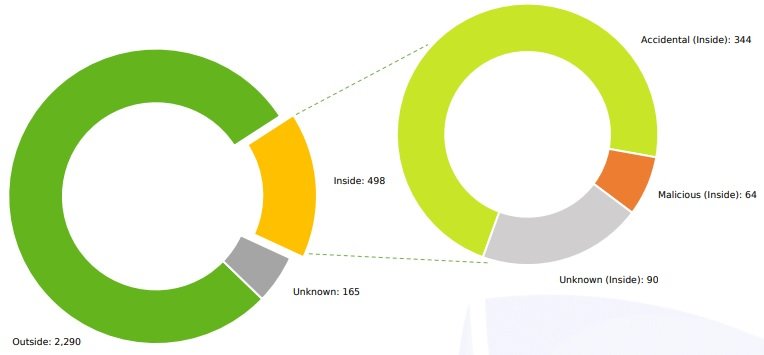
Organizations were able to strengthen their security practices by managing data storage deployments, although the main threat remains malicious hackers. The Risk Based Security report mentions that ransomware was one of the main causes of security incidents in 2020.
Inga Goddijn, a Risk Based Security specialist, believes that in the context of the 2020 US election, the cybersecurity industry as a whole seems less focused on addressing hacktivism than in 2016: “This could be due to general fatigue at the number of events recorded each week.”
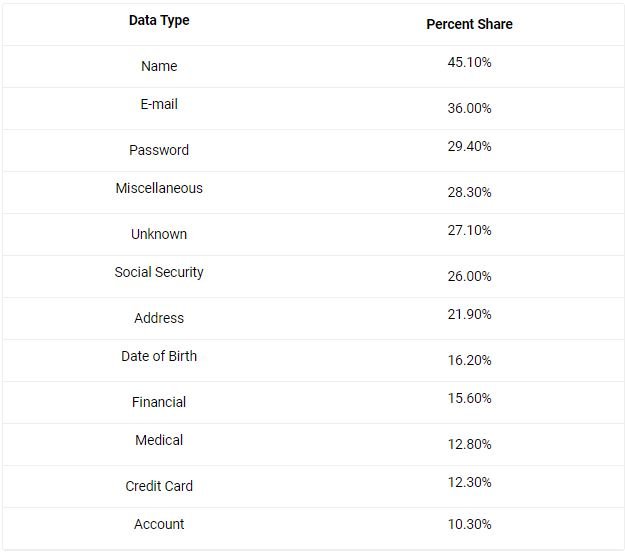
Personal information, the main objective
Personally identifiable data and financial information remain the most vulnerable records, as they are involved in most security incidents recorded this year.
The health services industry was the most attacked by hackers in 2020. Health organizations recorded a total of 341 security incidents, followed by the information services (306) and the finance and insurance sector (274). For their part, public administration and science organizations occupy the fourth (259) and fifth (242) posts, respectively.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.