Microsoft has released a report to recognize that a group of malicious hackers allegedly sponsored by the Iranian government successfully compromised the email accounts of some of the most prominent participants in the 2020 Munich Security Conference and the Think 20 conference.
The attack was targeted at more than 100 people and, according to the Microsoft Threat Intelligence Center (MSTIC), was deployed by the hacking group identified as Phosphorus, also known as Charming Kitten, APT 35 or Magic Hound.
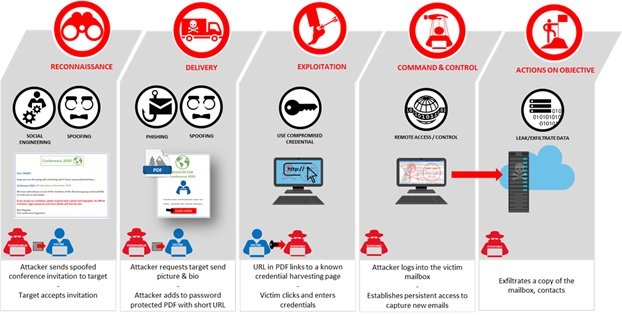
This attack would be part of a cyber espionage campaign that aims to collect information through the leak of emails from the participants of this summit, redirecting this information to two domains controlled by the threat actors (g20saudi.000webhostapp.com and ksat20.000webhostapp.com).
Hackers sent false invitations via email to former officials, policy specialists, academics and leaders of non-governmental organizations who would participate in the meeting, a campaign deployed for months. Unlike other phishing campaigns, the operators of this attack used near-perfect English in writing their messages, as well as legitimate-looking multimedia content.
Although MSTIC initially stated that there was no reason to think that this attack was related to the U.S. election, a campaign deployed a few weeks ago has made the company reconsider its stance. Microsoft reportedly found that some national state-sponsored hacker groups might be trying to intervene in the electoral process as happened in the previous election.
Tom Burt, Vice President of Customer Security and Trust at Microsoft, says, “We are working with conference organizers to take the required security measures and prevent similar behavior at other conferences or events.” Burt also recommended potential attack targets to verify the security of their email accounts to prevent theft of sensitive information.
The targeted security conference is known for bringing together hundreds of high-level decision makers and prominent opinion leaders from around the world, including heads of state, ministers, and leaders of non-governmental organizations.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
