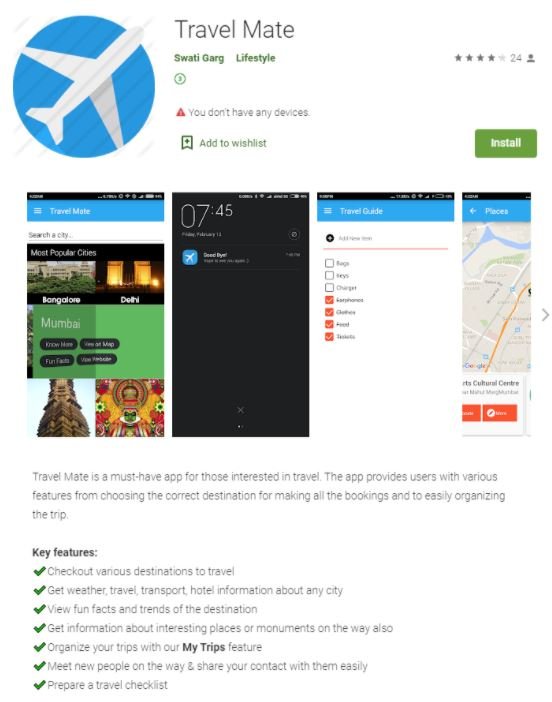
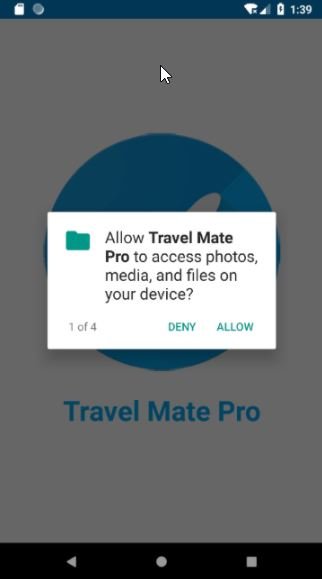
Kaspersky researchers have reported finding a sample of Android spyware that does not appear to have been detected previously; the sample was detected in a travel app for users in India. Subsequent analyses detected that this sample could be related to GravityRAT, a remote access Trojan (RAT) with a wide presence in Indian Territory with the ability to operate on multiple platforms, including Android and MacOS.
Detected in 2015, GravityRAT has been used in various high-profile attacks, including malicious campaigns targeting military officers in India. Although at first hackers seemed to target only Windows systems, its developers have made it a cross-platform tool.
The collected sample has been very useful for researchers to analyze all the changes made by the developers, so they have concluded that this is not a typical sample of Android software. The C&C scan revealed several additional malicious modules, also related to GravityRAT developers. In general, more than 10 versions of GravityRAT were found, distributed under the appearance of legitimate applications; jointly employed, modules allow threat actors to access compromised operating systems.
GravityRAT’s various modules can retrieve device data, browsing logs, contact lists, email addresses, call logs, and text messages. In addition, the Trojan looks for access to files with extensions such as .jpg, .jpeg, .log, .png, .txt, .pdf, .xml, .doc, .xls, .xlsx, .ppt, .pptx, .docx, and .opus.
The fact that GravityRAT has become a cross-platform threat is a clear sign of the development that its creators have achieved, so preventing an attack is critical.
To prevent any attempted attack, experts recommend avoiding downloading apps from unknown sources, as this is the main strategy of hackers to infect mobile users. On endpoint-level detection, experts recommend turning to traditional solutions to protect your networks from spy activity.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.