Cybersecurity specialists reported that the Windows Update client could be abused by threat actors to perform malicious code attacks on Windows systems. Using living-off-the-land binaries (LoLBins), malicious hackers bypass detection while they download, install and execute malicious code on target systems.
Besides, threat actors can also use this technique to bypass Windows User Account Control (UAC) or Windows Defender Application Control (WDAC), gaining persistence over the affected implementations.
The WSUS/Windows Update client is a utility located at %windir%\system32\ used to provides users partial control over some of the Windows Update Agent’s functionality from the command-line, allowing to look for new updates and install them, no Windows user interface needed.
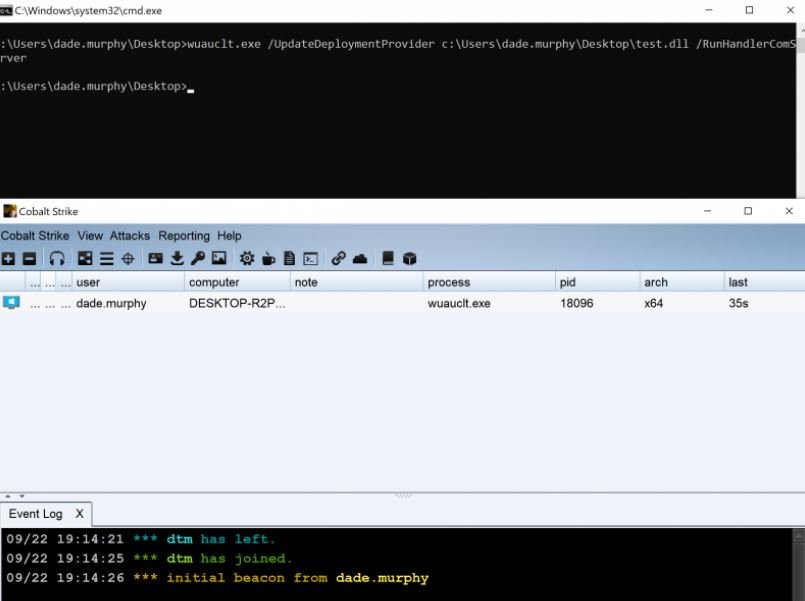
By using the /ResetAuthorization option, it allow initiating a manual update check either on the locally configured WSUS server or via the Windows Update service according to Microsoft. Information security specialists reported that wuauclt could be abused by threat actors to execute malicious code on vulnerable Windows 10 systems. To do so, hackers only need to send a specially crafted DLL with these command-line options:
wuauclt.exe /UpdateDeploymentProvider [path_to_dll] /RunHandlerComServer
The Full_Path_To_DLL is the main path to the malicious hackers’ specially crafted DLL file that would execute code after attaching it.
In case this technique is used to bypass antivirus solutions, hackers can do so by executing malicious code from a DLL loaded using a signed Microsoft binary, the Windows Update client. The attack has been detected in the wild.
Microsoft has released a patch to update Microsoft Defender, adding a way to download potentialy malicious files onto Wnidows devices.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
