In its most recent security report, Microsoft mentions that more than 13 billion suspicious phishing emails were sent and blocked during 2019, adding that 2020 figures could increase considerably due to the pandemic.
In its annual Digital Defense report, the company mentions that the most recent months have been a sign of the sophistication achieved by groups operating these attacks, using techniques that make it more difficult to detect potentially malicious email.

The report also emphasizes the transition that multiple hacking communities have made, as many changed malware attacks to phishing campaigns, which has also contributed to the increase in this activity: “More than one billion of these malicious emails were sent from URLs configured for this specific purpose,” the experts mention.
These attacks are primarily deployed to extract login credentials, but can also be leveraged to perform subsequent attacks such as malware infections, recognition, and exploitation of virtual private network (VPN) vulnerabilities. Another interesting finding is the increase in attacks related to Internet of Things (IoT) deployments, which increased by almost 35% compared to the previous year.
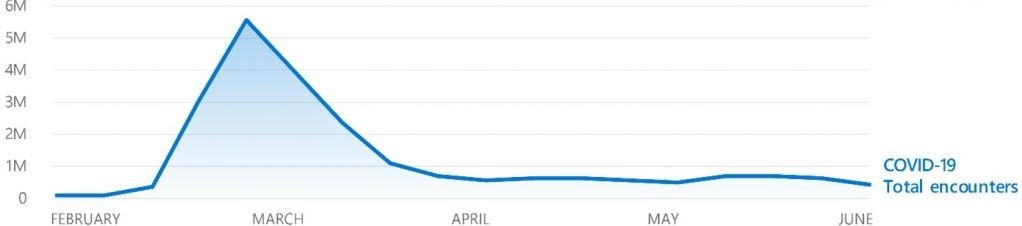
A determining factor for Microsoft’s expected increase is the COVID-19 pandemic, as threat actors have exploited this topic to send emails in bulk by offering purported vaccines, medications, or up-to-date information in real time to extract large amounts of sensitive information from people concerned about their health.
Although the biggest signs of phishing are found in China, Russia and the United States, this is a type of cyberattack that has spread virtually anywhere in the world.
Social distancing and work from home have also contributed to increased phishing attacks, as threat actors have found better ways to trick unsuspecting users into stealing their data, extracting sensitive information, and even deploying denial-of-service (DoS) attacks.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
