A new security risk has been reported for users of Amazon’s Alexa voice assistant. Apparently, just by clicking on a link the victims could provide access to the threat actors, which would allow them to spy on the user’s activities remotely.
A security team at the firm Check Point revealed these serious vulnerabilities that could allow multiple hacking variants.
In the report, the researchers claim that these exploits could have allowed threat actors to remove or install features in the target user’s Alexa account, access their voice history, and extract personal information by interacting with the software: “These devices have become so common that it’s easy to ignore the amount of information they store and the security issues that affect them” Roman Zaikin, a member of the research team, mentions Roman Zaikin. The flaws were reported to Amazon, which released a patch for remediation last month.
XSS failure across multiple subdomains of the company
Researchers attribute these flaws to a poorly implemented CORS policy in the voice assistant mobile app, which would allow malicious hackers with the ability to inject code into an Amazon subdomain to deploy a cross-site script attack (XSS), so attacking the target user would only require a specially crafted link.
The investigation also found that a request to retrieve a list of skills installed on the Alexa device returns a CSRF token in the response; this token exists to prevent cross-site request forgery attacks. This happens because the site cannot differentiate between legitimate applications and forged applications.
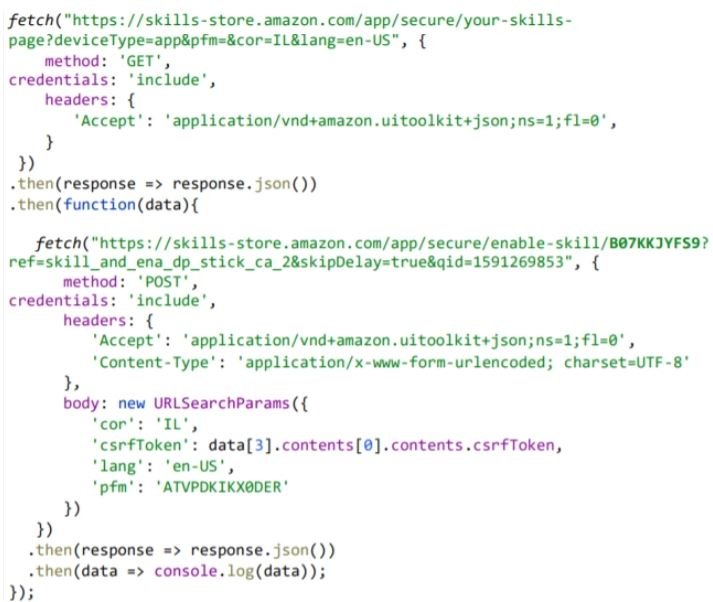
With the token in possession, a malicious hacker can create valid requests to the backend server and perform actions by impersonating the victim, such as installing and enabling new Alexa skills remotely. Simply put, the attack works by asking the user to click on a malicious link that navigates to an Amazon subdomain (‘track.amazon.com’) with an XSS flaw that can be exploited to achieve code injection.
Threat actors trigger a request to the “skillsstore.amazon.com” subdomain using the victim’s credentials to get a list of all the skills installed in the Alexa account and the CSRF token. Finally, the exploit captures the CSRF token from the response and uses it to install a new skill with a specific ID, which will operate stealthily.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
