The developers of the Zoom video conferencing platform announced the release of updates to address some security flaws in the Linux client. Successful exploitation of this flaw would have allowed threat actors to access the vulnerable system, read and extract data from users, as well as run malware disguised as a reliable application thread.
Mazin Ahmed, a researcher who assisted in finding these flaws, mentions that Zoom also exposed a poorly configured instance and had not received updates in nearly a year, so the application could still be exposed to uncorrected flaws exploitation. Ahmed notified his finding to the company, which published the corrections a few days ago.
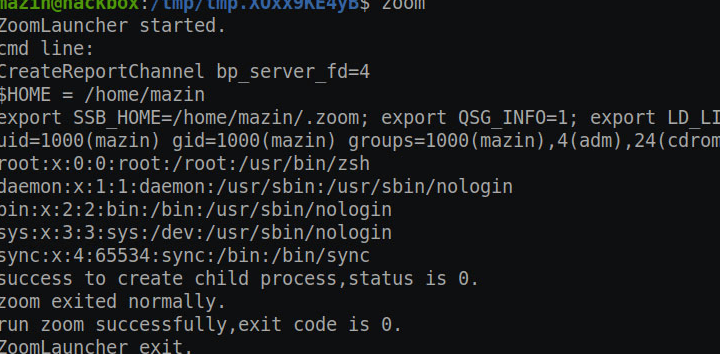
One of the attacks described by Ahmed targets Zoom Launcher for Linux, which could allow threat actors to run unauthorized software: “The whitelist of applications can be circumvented to run malware as a reliable thread, which represents a bad security practice,” the researcher says.
In another similar scenario, a malicious hacker with access to the target system could access the user’s confidential information, including messages stored in plain text. Other potential attacks are related to a weak authentication service and a TLS/SSL issue that would allow custom logs to be injected into the local Zoom database.
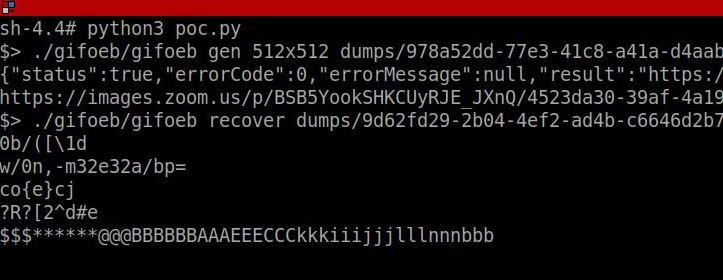
Ahmed’s report continues highlighting a memory leak vulnerability by exploiting the profile picture feature in Zoom to load a malicious GIF, download the rendered file, and extract its metadata to expose parts of the system memory.
Although Ahmed believes this is a consequence of a known flaw in ImageMagick image conversion software (CVE-2017-15277), Zoom ensures that the utility is not used to convertfs loaded as profile images in JPEG format.
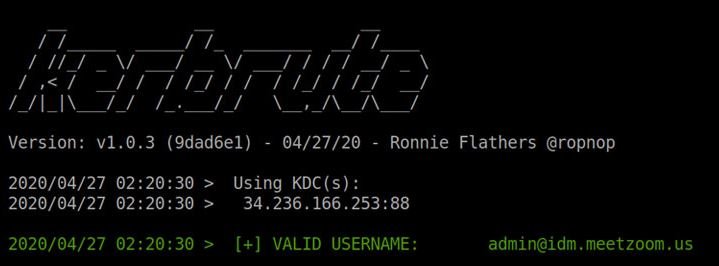
Zoom removed the exposed Kerberos authentication server to prevent brute force attacks, as well as implementing other solutions to address the lack of encryption when storing chat logs.
While most potential attacks depend on threat actors having previously compromised the target user’s device, specialists recommend that you do not ignore updates. The findings were presented in DEF CON 2020.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
