A few days ago, a dark web advertisement was released offering access to a Citrix customer database. In an official statement, the company denies that its internal networks were compromised by threat actors, noting that the incident occurred by a third party.
“Multiple reports of the sale of a Citrix database on dark web have recently appeared, erroneously implying a compromise in the security of the company”. The database includes more than 2 million records and is on sale for 2.15 Bitcoin (about 20 thousand dollars).
Citrix’s Fermin J. Serna added that “a threat intelligence report circulated on claims made in a dark web forum by a threat actor alleging compromise, data theft, and escalation of privilege attack attempts to launch Citrix systems’ ransomware infection.”
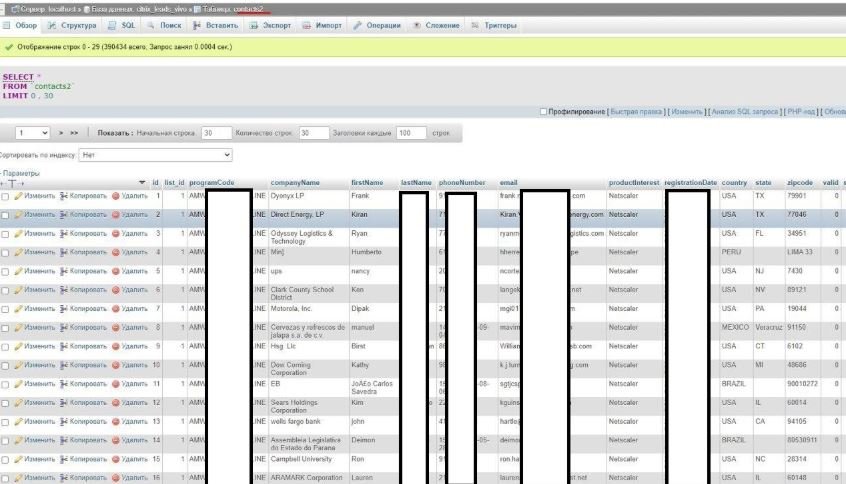
After an internal investigation, Citrix concluded that there are no compromise records in their networks. A subsequent investigation revealed that the incident occurred on a third-party network: “A third-party company suffered a security incident that resulted in the loss of one of our database. We have been in constant communication with the company involved.” The Citrix representative mentioned that unauthorized access to compromised information has already been closed.
The third party whose systems were compromised has also begun its own investigation, as well as implementing some additional security measures to prevent subsequent incidents. As the Citrix representative explains, the data breach in this company does not mean that Citrix networks were tapped by threat actors or that a company member’s login credentials were stolen.
This is not the first time Citrix information has been compromised. A year ago, the FBI discovered that a hacker group managed to access the company’s networks to extract sensitive data from employees and business customers, including full names, social security numbers, financial details, among others.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
