The pandemic has presented an ideal opportunity for many cybercriminals. According to a report from Microsoft, some hackers have tried to take advantage of the issues related to the coronavirus to try to trick employees of some companies into handing over access to their Office 365 accounts.
This week, a security team from the company revealed some details about this phishing campaign, deployed in about 65 different countries.
Microsoft claims that this campaign has been active since December 2019 and, although initially dealing with generic themes, after the massive COVID-19 outbreak phishing emails sent by these hackers began to employ similar subject lines to deceive users.
If users click on the attachments, they will be granting access to a malicious web application, which will be used in other attacks.

That malicious web application resembles a legitimate Microsoft platform, although the URL has nothing to do with the company. Hackers do not try to obtain the login credentials of the affected users, but try to get the victim to grant some access permissions to their Office 365 account, including the ability to read their emails or make changes to account settings.
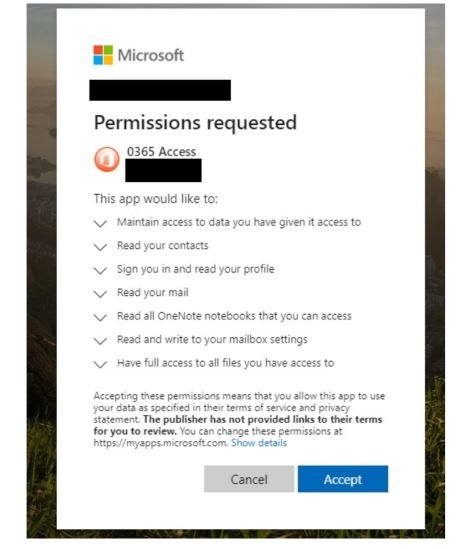
If users fall into the trap, their accounts will be completely exposed to an attack variant known as “commercial email compromise”, so hackers can perform new highly personalized phishing attacks with financial motivations. Hackers could also access sensitive company information.
The operators of this campaign have sent millions of emails in less than a year, thousands of them sent to major executives and managers at major private companies, as well as attacking prominent public institutions.
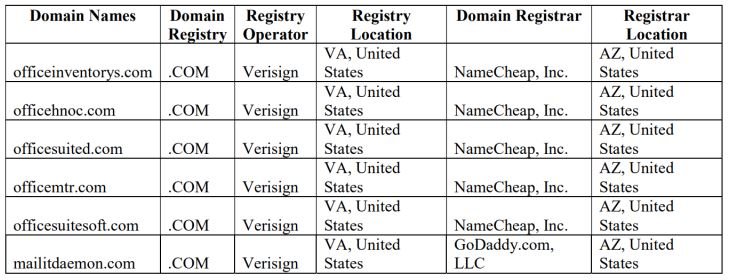
Microsoft’s security team has detected at least six domains controlled by threat actors, so the company began a legal process for authorities to take control of those resources. A couple of days ago, the U.S. District Court in Virginia granted control of these domains to Microsoft.
As a recommendation, technology and cybersecurity companies point out that users should never grant permissions to third-party applications, as depending on the nature of the account exposed hackers could gain access to sensitive personal and business information.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
