Ransomware infections are one of the main threats faced daily by users, public organizations and private companies. While the main targets of these hackers are desktop computers, malicious hackers are beginning to venture into creating ransomware for mobile devices.
The ‘Black Rose Lucy’ malware family discovered a couple of years ago, is one of the first ransomware attempts for Android devices. New attacks have recently been detected with this malware, which has evolved considerably, so it now has sophisticated features that allow you to take control of a target device and install malicious apps.
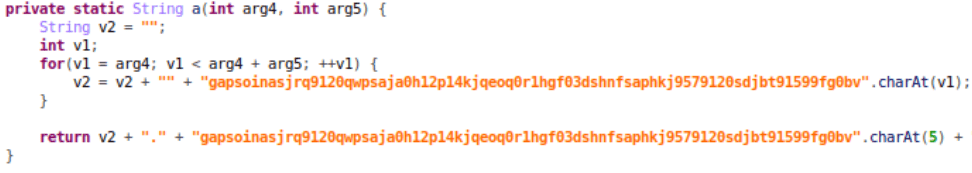
The malware starts by registering a receiver named “uyqtecppxr” to run BOOT_COMPLETE and QUICKBOOT_POWERON to verify if the device’s country code is from a former Soviet state.
Within the MainActivity module, the application activates the malicious service, which then registers a BroadcastReceiver that is called by the command action. SCREEN_ON and then he calls himself. This is used to purchase the “WakeLock” service, which keeps the device screen turned on, and the “WifiLock” service, which keeps the device’s WiFi on.
The malware has 4 command and control (C&C) encrypted servers in its code. Unlike previous versions of Lucy, this C&C is a domain and not an IP address, so even though the server may collapse, it can easily resolve to a new IP address, making it much harder to neutralize malware.
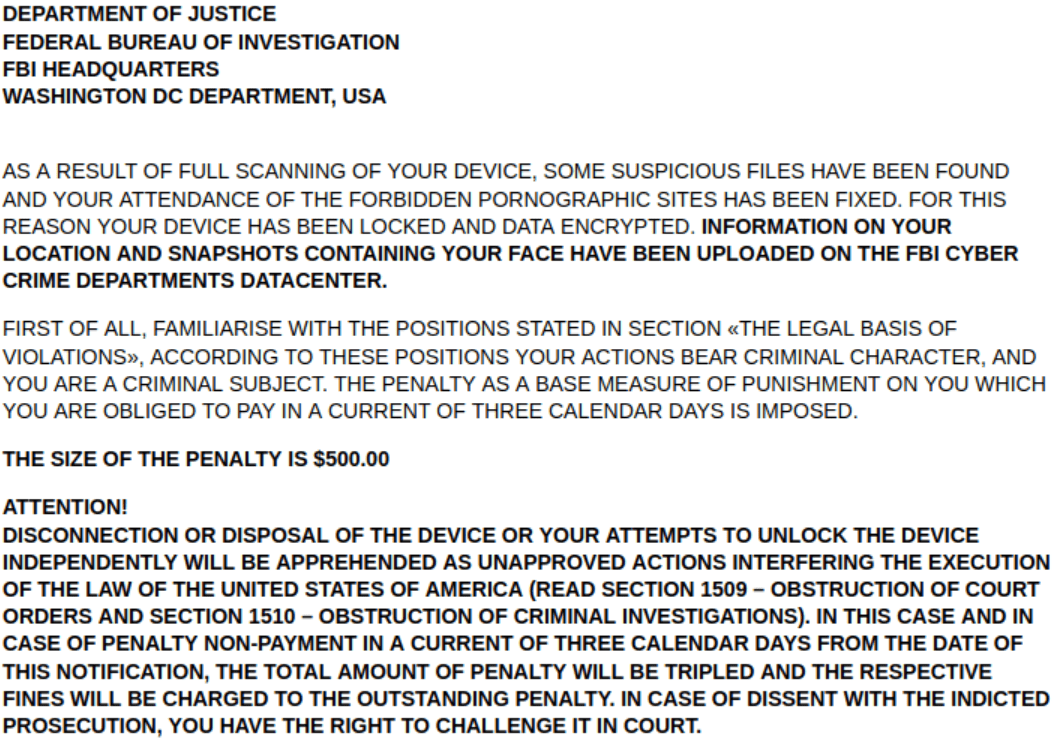
When downloaded, the Lucy malware begins to encrypt the files on the target device, then display a ransom note in the browser. A noteworthy feature is that this message is displayed as if it were an accusation of illegal material possession (piracy, child pornography, among others).
The FBI’s false message also assures the victim that their data is being sent to the agency’s Cybercrime Department Data Center, along with a report of alleged illegal conduct.
Regarding their ability to enter the target device, Lucy’s operators use a very cunning method: To get started, they display a message asking the user to turn on the Streaming Video Optimization (SVO) feature. By clicking “OK”, the target user grants the malware permission to use the accessibility service, so smartphone encryption is only a matter of time. Files encrypted with this malware receive the extension .Lucy.

At the end of the encryption of the information, the ransom note sent by the hackers is displayed. Finally, the victim is told to pay a $500 “fine” and is asked to provide their credit card information and how to purchase Bitcoin for ransom payment.
While ransomware for mobile devices has not yet made great strides, it is possible to find some evolution. Lucy is a sign of the diversification capabilities of threat actors, cybersecurity specialists claimed, and experts fear that a campaign of massive ransomware attacks against mobile users could soon arrive.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
